
(Edit 2023-05-10: This has now
launched for a subset of Twitter users. The code that existed to notify users that device identities had changed does not appear to have been enabled - as a result, in its current form, Twitter can absolutely MITM conversations and read your messages)
Elon Musk appeared on an interview with Tucker Carlson last month, with one of the topics being the fact that Twitter could be legally compelled to hand over users' direct messages to government agencies since they're held on Twitter's servers and aren't encrypted. Elon talked about how they were in the process of implementing proper encryption for DMs that would prevent this - "You could put a gun to my head and I couldn't tell you. That's how it should be."
tl;dr - in the current implementation, while Twitter
could subvert the end-to-end nature of the encryption, it could not do so without users being notified. If any user involved in a conversation were to ignore that notification,
all messages in that conversation (including ones sent in the past) could then be decrypted. This isn't ideal, but it still seems like an improvement over having no encryption at all. More technical discussion follows.
For context: all information about Twitter's implementation here has been derived from reverse engineering version 9.86.0 of the Android client and 9.56.1 of the iOS client (the current versions at time of writing), and the feature hasn't yet launched. While it's certainly possible that there could be major changes in the protocol between now launch, Elon has asserted that they plan to launch the feature this week so it's plausible that this reflects what'll ship.
For it to be impossible for Twitter to read DMs, they need to not only be encrypted, they need to be encrypted with a key that's not available to Twitter. This is what's referred to as "end-to-end encryption", or e2ee - it means that the only components in the communication chain that have access to the unencrypted data are the endpoints. Even if the message passes through other systems (and even if it's
stored on other systems), those systems do not have access to the keys that would be needed to decrypt the data.
End-to-end encrypted messengers were initially popularised by
Signal, but the Signal protocol has since been incorporated into
WhatsApp and is probably much more widely used there. Millions of people per day are sending messages to each other that pass through servers controlled by third parties, but those third parties are completely unable to read the contents of those messages. This is the scenario that Elon described, where there's no degree of compulsion that could cause the people relaying messages to and from people to decrypt those messages afterwards.
But for this to be possible, both ends of the communication need to be able to encrypt messages in a way the other end can decrypt. This is usually performed using
AES, a well-studied encryption algorithm with no known significant weaknesses. AES is a form of what's referred to as a symmetric encryption, one where encryption and decryption are performed with the same key. This means that both ends need access to that key, which presents us with a bootstrapping problem. Until a shared secret is obtained, there's no way to communicate securely, so how do we generate that shared secret? A common mechanism for this is something called
Diffie Hellman key exchange, which makes use of asymmetric encryption. In asymmetric encryption, an encryption key can be split into two components - a public key and a private key. Both devices involved in the communication combine their private key and the other party's public key to generate a secret that can only be decoded with access to the private key. As long as you know the other party's public key, you can now securely generate a shared secret with them. Even a third party with access to all the public keys won't be able to identify this secret. Signal makes use of a variation of Diffie-Hellman called
Extended Triple Diffie-Hellman that has some desirable properties, but it's not
strictly necessary for the implementation of something that's end-to-end encrypted.
Although it was
rumoured that Twitter would make use of the Signal protocol, and in fact there are vestiges of code in the Twitter client that still reference Signal, recent versions of the app have shipped with an entirely different approach that appears to have been written from scratch. It seems simple enough. Each device generates an asymmetric keypair using the NIST P-256 elliptic curve, along with a device identifier. The device identifier and the public half of the key are uploaded to Twitter using a new API endpoint called
/1.1/keyregistry/register. When you want to send an encrypted DM to someone, the app calls
/1.1/keyregistry/extract_public_keys with the IDs of the users you want to communicate with, and gets back a list of their public keys. It then looks up the conversation ID (a numeric identifier that corresponds to a given DM exchange - for a 1:1 conversation between two people it doesn't appear that this ever changes, so if you DMed an account 5 years ago and then DM them again now from the same account, the conversation ID will be the same) in a local database to retrieve a conversation key. If that key doesn't exist yet, the sender generates a random one. The message is then encrypted with the conversation key using AES in GCM mode, and the conversation key is then put through Diffie-Hellman with each of the recipients' public device keys. The encrypted message is then sent to Twitter along with the list of encrypted conversation keys. When each of the recipients' devices receives the message it checks whether it already has a copy of the conversation key, and if not performs its half of the Diffie-Hellman negotiation to decrypt the encrypted conversation key. One it has the conversation key it decrypts it and shows it to the user.
What would happen if Twitter changed the registered public key associated with a device to one where they held the private key, or added an entirely new device to a user's account? If the app were to just happily send a message with the conversation key encrypted with that new key, Twitter would be able to decrypt that and obtain the conversation key. Since the conversation key is tied to the conversation, not any given pair of devices, obtaining the conversation key means you can then decrypt every message in that conversation, including ones sent before the key was obtained.
(An aside: Signal and WhatsApp make use of a protocol called
Sesame which involves additional secret material that's shared between every device a user owns, hence why you have to do that QR code dance whenever you add a new device to your account. I'm grossly over-simplifying how clever the Signal approach is here, largely because I don't understand the details of it myself. The Signal protocol uses something called the
Double Ratchet Algorithm to implement the actual message encryption keys in such a way that even if someone were able to successfully impersonate a device they'd only be able to decrypt messages sent after that point even if they had encrypted copies of every previous message in the conversation)
How's this avoided? Based on the UI that exists in the iOS version of the app, in a fairly straightforward way - each user can only have a single device that supports encrypted messages. If the user (or, in our hypothetical, a malicious Twitter) replaces the device key, the client will generate a notification. If the user pays attention to that notification and verifies with the recipient through some out of band mechanism that the device has actually been replaced, then everything is fine. But, if
any participant in the conversation ignores this warning, the holder of the subverted key can obtain the conversation key and decrypt the entire history of the conversation. That's strictly worse than anything based on Signal, where such impersonation would simply not work, but even in the Twitter case it's not possible for someone to silently subvert the security.
So when Elon says Twitter wouldn't be able to decrypt these messages even if someone held a gun to his head, there's a condition applied to that - it's true as long as nobody fucks up. This is clearly better than the messages just not being encrypted at all in the first place, but overall it's a weaker solution than Signal. If you're currently using Twitter DMs, should you turn on encryption? As long as the limitations aren't too limiting, definitely! Should you use this in preference to Signal or WhatsApp? Almost certainly not. This seems like a genuine incremental improvement, but it'd be easy to interpret what Elon says as providing stronger guarantees than actually exist.

comments

 From May 25th to 27th, Bras lia hosted the
MiniDebConf 2023. This gathering, composed
of various activities such as talks, workshops, sprints, BSP (Bug Squashing
Party), key signing, social events, and hacking, aimed to bring the community
together and celebrate the world's largest Free Software project: Debian.
The MiniDebConf Bras lia 2023 was a success thanks to the participation of
everyone, regardless of their level of knowledge about Debian. We valued the
presence of both beginners who are getting familiar with the system and official
project developers. The spirit of inclusion and collaboration was present
throughout the event.
MiniDebConfs are local meetings organized by members of the Debian Project,
aiming to achieve similar goals as DebConf but on a regional scale. Throughout
the year, events like this occur in different parts of the world, strengthening
the Debian community.
From May 25th to 27th, Bras lia hosted the
MiniDebConf 2023. This gathering, composed
of various activities such as talks, workshops, sprints, BSP (Bug Squashing
Party), key signing, social events, and hacking, aimed to bring the community
together and celebrate the world's largest Free Software project: Debian.
The MiniDebConf Bras lia 2023 was a success thanks to the participation of
everyone, regardless of their level of knowledge about Debian. We valued the
presence of both beginners who are getting familiar with the system and official
project developers. The spirit of inclusion and collaboration was present
throughout the event.
MiniDebConfs are local meetings organized by members of the Debian Project,
aiming to achieve similar goals as DebConf but on a regional scale. Throughout
the year, events like this occur in different parts of the world, strengthening
the Debian community.
 Activities
The MiniDebConf program was intense and diverse. On May 25th and 26th (Thursday
and Friday), we had talks, discussions, workshops, and many hands-on activities.
On the 27th (Saturday), the Hacking Day took place, which was a special moment
for Debian contributors to come together and work collaboratively on various
aspects of the project. This was the Brazilian version of Debcamp, a tradition
preceding DebConf. On this day, we prioritized practical activities such as
software packaging, translations, key signing, install fest, and the Bug
Squashing Party.
Activities
The MiniDebConf program was intense and diverse. On May 25th and 26th (Thursday
and Friday), we had talks, discussions, workshops, and many hands-on activities.
On the 27th (Saturday), the Hacking Day took place, which was a special moment
for Debian contributors to come together and work collaboratively on various
aspects of the project. This was the Brazilian version of Debcamp, a tradition
preceding DebConf. On this day, we prioritized practical activities such as
software packaging, translations, key signing, install fest, and the Bug
Squashing Party.

 Edition numbers
The event numbers are impressive and demonstrate the community's involvement
with Debian. We had 236 registered participants, 20 submitted talks, 14
volunteers, and 125 check-ins. Furthermore, in the hands-on activities, we
achieved significant results, including 7 new installations of Debian GNU/Linux,
the update of 18 packages in the official Debian project repository by
participants, and the inclusion of 7 new contributors to the translation team.
We also highlight the remote participation of the community through live
streams. The analytics data reveals that our website received a total of 7,058
views, with 2,079 views on the homepage (which featured our sponsors' logos),
3,042 views on the program page, and 104 views on the sponsors' page. We
recorded 922 unique users during the event.
On YouTube, the live stream reached 311 views, with 56 likes and a peak of 20
concurrent views. There were an incredible 85.1 hours of watch time, and our
channel gained 30 new subscribers. All this engagement and interest from the
community further strengthen MiniDebConf.
Edition numbers
The event numbers are impressive and demonstrate the community's involvement
with Debian. We had 236 registered participants, 20 submitted talks, 14
volunteers, and 125 check-ins. Furthermore, in the hands-on activities, we
achieved significant results, including 7 new installations of Debian GNU/Linux,
the update of 18 packages in the official Debian project repository by
participants, and the inclusion of 7 new contributors to the translation team.
We also highlight the remote participation of the community through live
streams. The analytics data reveals that our website received a total of 7,058
views, with 2,079 views on the homepage (which featured our sponsors' logos),
3,042 views on the program page, and 104 views on the sponsors' page. We
recorded 922 unique users during the event.
On YouTube, the live stream reached 311 views, with 56 likes and a peak of 20
concurrent views. There were an incredible 85.1 hours of watch time, and our
channel gained 30 new subscribers. All this engagement and interest from the
community further strengthen MiniDebConf.
 Photos and videos
To relive the best moments of the event, we have photos and recordings
available. Photos can be accessed at: https://deb.li/pbsb2023. Video recordings
of the talks are available at the following link: https://deb.li/vbsb2023.
To stay updated and connect with the Debian Bras lia community, follow us on
our social media channels:
Photos and videos
To relive the best moments of the event, we have photos and recordings
available. Photos can be accessed at: https://deb.li/pbsb2023. Video recordings
of the talks are available at the following link: https://deb.li/vbsb2023.
To stay updated and connect with the Debian Bras lia community, follow us on
our social media channels:
 MiniDebConf Bras lia 2023 was a milestone for the Debian community,
demonstrating the power of collaboration and Free Software. We hope that
everyone enjoyed this enriching gathering and will continue to actively
participate in future Debian Project initiatives. Together, we can make a
difference!
MiniDebConf Bras lia 2023 was a milestone for the Debian community,
demonstrating the power of collaboration and Free Software. We hope that
everyone enjoyed this enriching gathering and will continue to actively
participate in future Debian Project initiatives. Together, we can make a
difference!

 Since before I got involved in the eID
Since before I got involved in the eID  So
So  Last night I attended the first local Linux User Group talk since before the pandemic (possibly even long before the pandemic!)
Topic: How and why Atomic Access runs Debian on a 100Gbps router
Speaker: Joe Botha
This is the first time CLUG used
Last night I attended the first local Linux User Group talk since before the pandemic (possibly even long before the pandemic!)
Topic: How and why Atomic Access runs Debian on a 100Gbps router
Speaker: Joe Botha
This is the first time CLUG used 

 For DebConf23, we're pleased to announce opening of registration and call for proposal. Following is the info text -
For DebConf23, we're pleased to announce opening of registration and call for proposal. Following is the info text -

 The second release of the
The second release of the  I m calling time on DNSSEC. Last week, prompted by a change in my DNS hosting setup, I began removing it from the few personal zones I had signed. Then this Monday the .nz ccTLD experienced a
I m calling time on DNSSEC. Last week, prompted by a change in my DNS hosting setup, I began removing it from the few personal zones I had signed. Then this Monday the .nz ccTLD experienced a  I write letters. The kind that are written on paper with a dip pen
I write letters. The kind that are written on paper with a dip pen  I ve also added a few pages for the addresses of my correspondents (and an index of the letters I ve exchanged with them), and a few empty pages for other notes.
Then I ve used my
I ve also added a few pages for the addresses of my correspondents (and an index of the letters I ve exchanged with them), and a few empty pages for other notes.
Then I ve used my  After printing (an older version where some of the pages are repeated. whoops, but it only happened 4 times, and it s not a big deal), it was time for binding this into a book.
I ve opted for Coptic stitch, so that the book will open completely flat and writing on it will be easier and the covers are 2 mm cardboard covered in linen-look bookbinding paper (sadly I no longer have a source for bookbinding cloth made from actual cloth).
After printing (an older version where some of the pages are repeated. whoops, but it only happened 4 times, and it s not a big deal), it was time for binding this into a book.
I ve opted for Coptic stitch, so that the book will open completely flat and writing on it will be easier and the covers are 2 mm cardboard covered in linen-look bookbinding paper (sadly I no longer have a source for bookbinding cloth made from actual cloth).
 I tried to screenprint a simple design on the cover: the first attempt was unusable (the paper was smaller than the screen, so I couldn t keep it in the right place and moved as I was screenprinting); on the second attempt I used some masking tape to keep the paper in place, and they were a bit better, but I need more practice with the technique.
Finally, I decided that for such a Victorian thing I will use an Iron-gall ink, but it s Rohrer & Knlingner Scabiosa, with a purple undertone, because life s too short to use blue-black ink :D
And now, I m off to write an actual letter, rather than writing online about things that are related to letter writing.
I tried to screenprint a simple design on the cover: the first attempt was unusable (the paper was smaller than the screen, so I couldn t keep it in the right place and moved as I was screenprinting); on the second attempt I used some masking tape to keep the paper in place, and they were a bit better, but I need more practice with the technique.
Finally, I decided that for such a Victorian thing I will use an Iron-gall ink, but it s Rohrer & Knlingner Scabiosa, with a purple undertone, because life s too short to use blue-black ink :D
And now, I m off to write an actual letter, rather than writing online about things that are related to letter writing.

 I do try not to report because right now every other day we see somewhere or the other the Govt. curtailing our rights and most people are mute
I do try not to report because right now every other day we see somewhere or the other the Govt. curtailing our rights and most people are mute  (Edit 2023-05-10: This has now
(Edit 2023-05-10: This has now  This post serves as a report from my attendance to Kubecon and CloudNativeCon 2023 Europe that took place in
Amsterdam in April 2023. It was my second time physically attending this conference, the first one was in
Austin, Texas (USA) in 2017. I also attended once in a virtual fashion.
The content here is mostly generated for the sake of my own recollection and learnings, and is written from
the notes I took during the event.
The very first session was the opening keynote, which reunited the whole crowd to bootstrap the event and
share the excitement about the days ahead. Some astonishing numbers were announced: there were more than
10.000 people attending, and apparently it could confidently be said that it was the largest open source
technology conference taking place in Europe in recent times.
It was also communicated that the next couple iteration of the event will be run in China in September 2023
and Paris in March 2024.
More numbers, the CNCF was hosting about 159 projects, involving 1300 maintainers and about 200.000
contributors. The cloud-native community is ever-increasing, and there seems to be a strong trend in the
industry for cloud-native technology adoption and all-things related to PaaS and IaaS.
The event program had different tracks, and in each one there was an interesting mix of low-level and higher
level talks for a variety of audience. On many occasions I found that reading the talk title alone was not
enough to know in advance if a talk was a 101 kind of thing or for experienced engineers. But unlike in
previous editions, I didn t have the feeling that the purpose of the conference was to try selling me
anything. Obviously, speakers would make sure to mention, or highlight in a subtle way, the involvement of a
given company in a given solution or piece of the ecosystem. But it was non-invasive and fair enough for me.
On a different note, I found the breakout rooms to be often small. I think there were only a couple of rooms
that could accommodate more than 500 people, which is a fairly small allowance for 10k attendees. I realized
with frustration that the more interesting talks were immediately fully booked, with people waiting in line
some 45 minutes before the session time. Because of this, I missed a few important sessions that I ll
hopefully watch online later.
Finally, on a more technical side, I ve learned many things, that instead of grouping by session I ll group
by topic, given how some subjects were mentioned in several talks.
On gitops and CI/CD pipelines
Most of the mentions went to
This post serves as a report from my attendance to Kubecon and CloudNativeCon 2023 Europe that took place in
Amsterdam in April 2023. It was my second time physically attending this conference, the first one was in
Austin, Texas (USA) in 2017. I also attended once in a virtual fashion.
The content here is mostly generated for the sake of my own recollection and learnings, and is written from
the notes I took during the event.
The very first session was the opening keynote, which reunited the whole crowd to bootstrap the event and
share the excitement about the days ahead. Some astonishing numbers were announced: there were more than
10.000 people attending, and apparently it could confidently be said that it was the largest open source
technology conference taking place in Europe in recent times.
It was also communicated that the next couple iteration of the event will be run in China in September 2023
and Paris in March 2024.
More numbers, the CNCF was hosting about 159 projects, involving 1300 maintainers and about 200.000
contributors. The cloud-native community is ever-increasing, and there seems to be a strong trend in the
industry for cloud-native technology adoption and all-things related to PaaS and IaaS.
The event program had different tracks, and in each one there was an interesting mix of low-level and higher
level talks for a variety of audience. On many occasions I found that reading the talk title alone was not
enough to know in advance if a talk was a 101 kind of thing or for experienced engineers. But unlike in
previous editions, I didn t have the feeling that the purpose of the conference was to try selling me
anything. Obviously, speakers would make sure to mention, or highlight in a subtle way, the involvement of a
given company in a given solution or piece of the ecosystem. But it was non-invasive and fair enough for me.
On a different note, I found the breakout rooms to be often small. I think there were only a couple of rooms
that could accommodate more than 500 people, which is a fairly small allowance for 10k attendees. I realized
with frustration that the more interesting talks were immediately fully booked, with people waiting in line
some 45 minutes before the session time. Because of this, I missed a few important sessions that I ll
hopefully watch online later.
Finally, on a more technical side, I ve learned many things, that instead of grouping by session I ll group
by topic, given how some subjects were mentioned in several talks.
On gitops and CI/CD pipelines
Most of the mentions went to  On etcd, performance and resource management
I attended a talk focused on etcd performance tuning that was very encouraging. They were basically talking
about the
On etcd, performance and resource management
I attended a talk focused on etcd performance tuning that was very encouraging. They were basically talking
about the 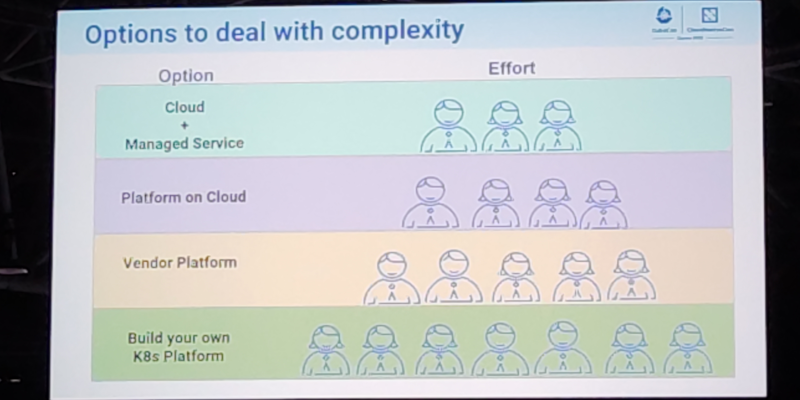 On jobs
I attended a couple of talks that were related to HPC/grid-like usages of Kubernetes. I was truly impressed
by some folks out there who were using Kubernetes Jobs on massive scales, such as to train machine learning
models and other fancy AI projects.
It is acknowledged in the community that the early implementation of things like Jobs and CronJobs had some
limitations that are now gone, or at least greatly improved. Some new functionalities have been added as
well. Indexed Jobs, for example, enables each Job to have a number (index) and process a chunk of a larger
batch of data based on that index. It would allow for full grid-like features like sequential (or again,
indexed) processing, coordination between Job and more graceful Job restarts. My first reaction was: Is that
something we would like to enable in
On jobs
I attended a couple of talks that were related to HPC/grid-like usages of Kubernetes. I was truly impressed
by some folks out there who were using Kubernetes Jobs on massive scales, such as to train machine learning
models and other fancy AI projects.
It is acknowledged in the community that the early implementation of things like Jobs and CronJobs had some
limitations that are now gone, or at least greatly improved. Some new functionalities have been added as
well. Indexed Jobs, for example, enables each Job to have a number (index) and process a chunk of a larger
batch of data based on that index. It would allow for full grid-like features like sequential (or again,
indexed) processing, coordination between Job and more graceful Job restarts. My first reaction was: Is that
something we would like to enable in 
 While I am not the biggest fan of Docker, I must admit it has quite some reach across various service providers and can often be seen as an API for running things in isolated environments.
One such service provider is GitHub when it comes to their Actions service.
I have no idea what isolation technology GitHub uses on the outside of Actions, but inside you just get an Ubuntu system and can run whatever you want via Docker as that comes pre-installed and pre-configured. This especially means you can run things inside vanilla Debian containers, that are free from any GitHub or Canonical modifications one might not want ;-)
So, if you want to run, say,
While I am not the biggest fan of Docker, I must admit it has quite some reach across various service providers and can often be seen as an API for running things in isolated environments.
One such service provider is GitHub when it comes to their Actions service.
I have no idea what isolation technology GitHub uses on the outside of Actions, but inside you just get an Ubuntu system and can run whatever you want via Docker as that comes pre-installed and pre-configured. This especially means you can run things inside vanilla Debian containers, that are free from any GitHub or Canonical modifications one might not want ;-)
So, if you want to run, say,